Threat Modeling
Threat Modeling Process and Design, DFD's

8-27 Plan
- Agenda
- Review Pre-test Assessment
- Review Web Architecture
- Discuss Tools
- Introduce Threat Modeling
- Objectives
- Understanding Threat Modeling and Why do we do it
- Challenges to Threat Modeling
- Precursors to Threat Modeling
What is Web Threat Modeling?
Threat Modeling
- Highly Conceptual
- Time consuming process - and should be embedded into SDLC
- Consider not important in past - More recently, gaining alot of traction
Threat Model - When and Where
SDLC Process
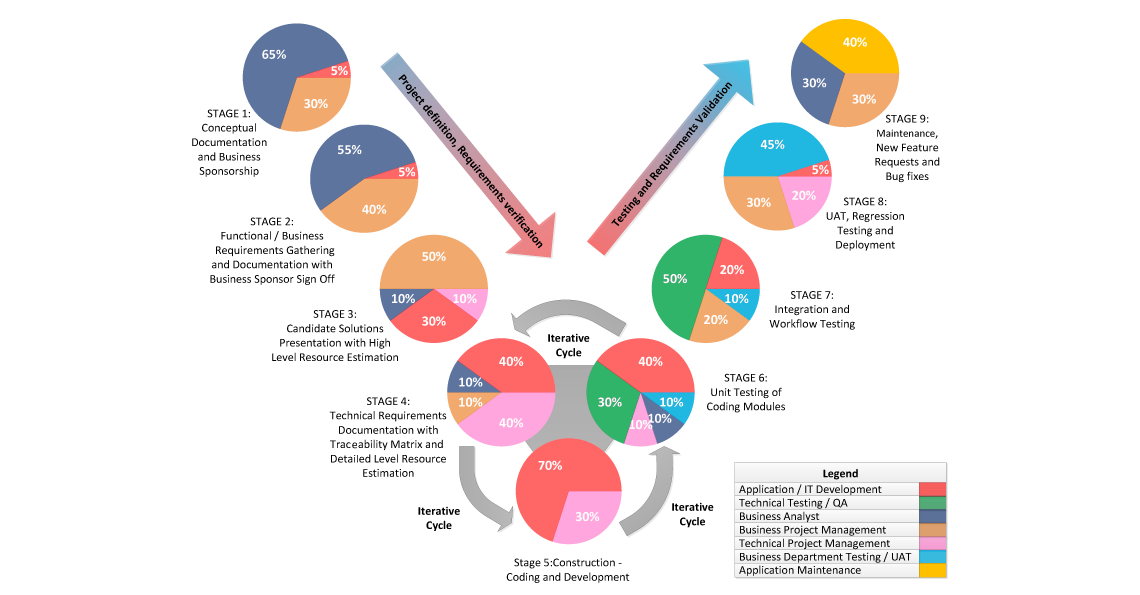
OWASP Presentation
OWASP Advanced Threat Modeling Slides
Example of DFD
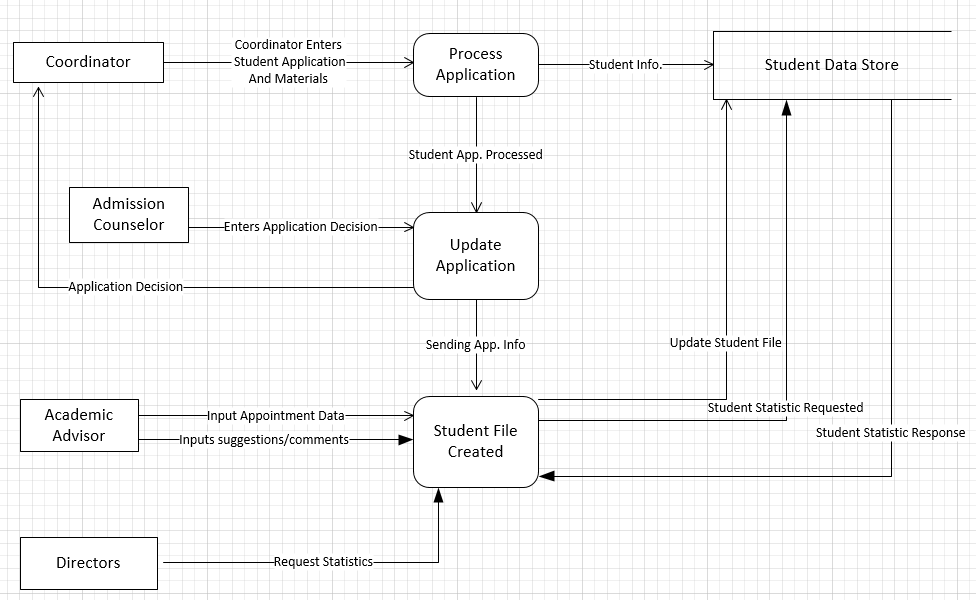
The focus is primarily the flow of data.
What is the difference between DFD's and Threat Model Diagrams?
Terminology
Limitations
Threat Agent
Assets
Mitigations
Security Controls
Attack Vector
Attack Trees
Trust Boundary
Data Flow Diagram
General TM Example
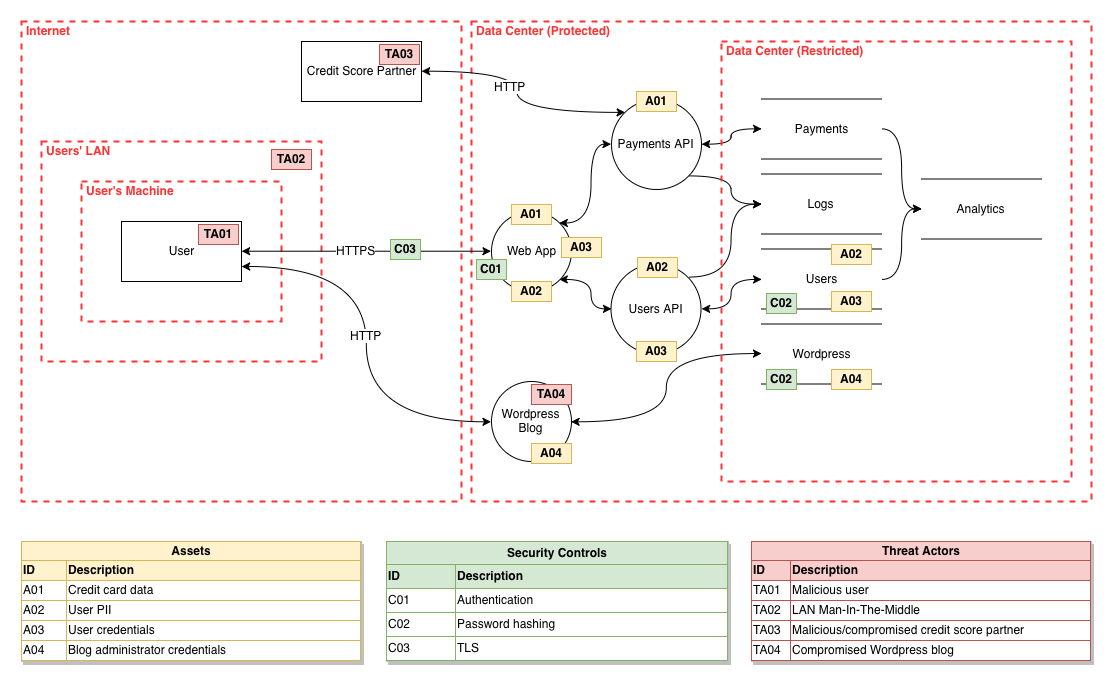
MPLSrenters.com TM diagram
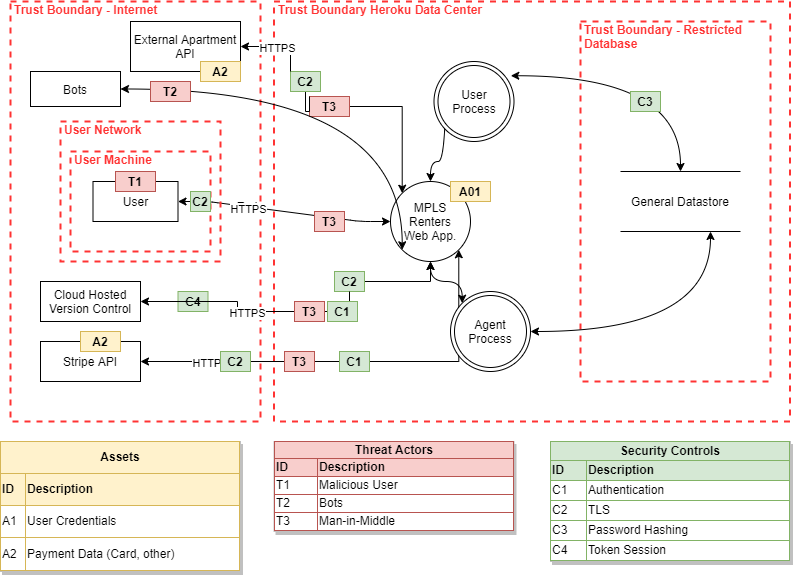
SLA's should take into threats and attacks into considerations
Not Depicted is Data classification