Http(s)/http/2 + TLS/SSL
Data-in-Transit & Encryption

Objectives
- Terminology
- Http(s)/Http2
- What is Hypertext Transfer Protocol?
- Request and Response Objects
- Encryption + TLS/SSL
- Encryption - Asymmetric Encryption | Symmetric Encryption | Hash Functions
- TLS/SSL Handshake
- Certificate Authorities
Question 1
Uses the same key to encrypt and decrypt a message?
- A. asymmetric encryption
- B. symmetric encryption
- C. hash function
- D. cipher suite
Question 2
Term used for data prior to encryption?
- A. cipher text
- B. data-in-transit
- C. default text
- E. plain text
Ton's of Acronyms - Activity
Http(s)
TCP
TLS
CSR
MAC
EV Cert.
CA
DNS
ECDHE
Http/Http(s)
Hypertext Transfer Protocol

an application layer protocol designed to transfer information between networked devices and runs on top of other layers of the network protocol stack.
http
- protocol for transmitting hypermedia documents, such as HTML[Data-in-Transit - Plain text]
https
- is encrypted in order to increase security of data transfer [Data-in-transit - cipher text]
http/2
- modifies how the data is formatted (framed) and transported between the client and server, both of which manage the entire process, and hides all the complexity from our applications within the new framing layer
HTTP/2 overview
The primary goals for HTTP/2 are to reduce latency by enabling full request and response multiplexing, minimize protocol overhead via efficient compression of HTTP header fields, and add support for request prioritization and server push.

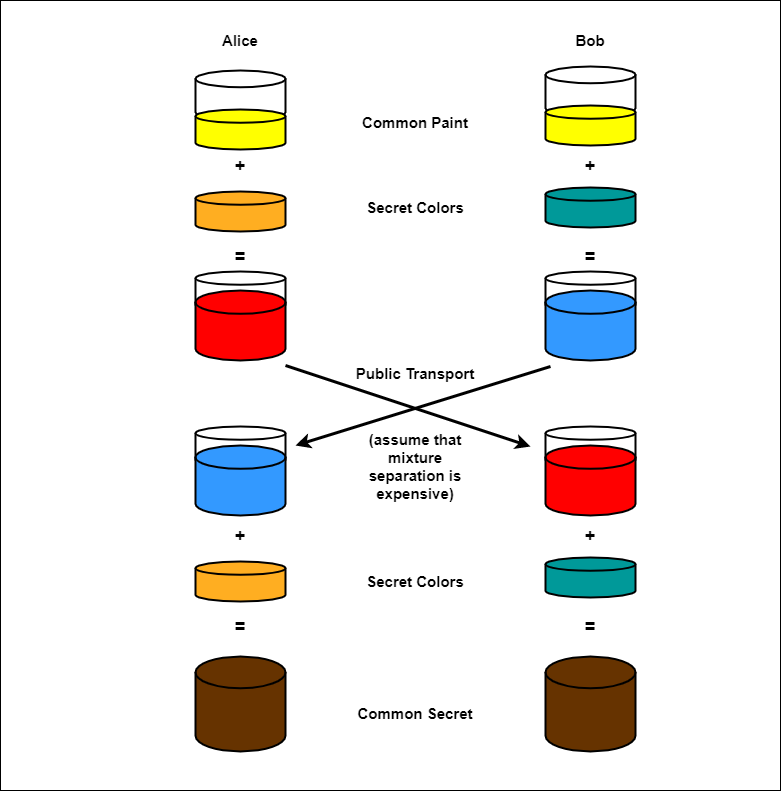
Encryption
Encryption Algorithm takes input data and scrambles it by using an encryption key - a secret between two parties
Symmetric
- - Uses the same key to encrypt and decrypt data
- Operate as block ciphers they break the input data into fixed-size blocks that can be individually encrypted
Asymmetric
- - Uses different keys to encrypt and decrypt data.
- Sometimes called public-key cryptography the encryption key (public key) can be published; only the decryption key (private key) needs to be kept secret.
Symmetric vs. Asymmetric
Visual without going into much detail
Hash Functions
Cryptographic hash functions which can be thought of as encryption algorithms whose output cannot be decrypted.
Using hashing algorithms is typically how passwords are stored in a database. The web server store the hashed value of the password in the database but will deliberately forget the actuall password value.

What is this below?
ECDHE-ECDSA-AES128-GCM-SHA256
Cipher Suites
A set of algorithms used to secure communication - Consist of three separate algorithms

key-exchange algorithm
asymmetric encryption algorithm used to exchange secret keys
Symmetric algorithm
block cipher designed for encrypting the content of TCP packets
MAC Algorithm
authenticating the encrypted messages.
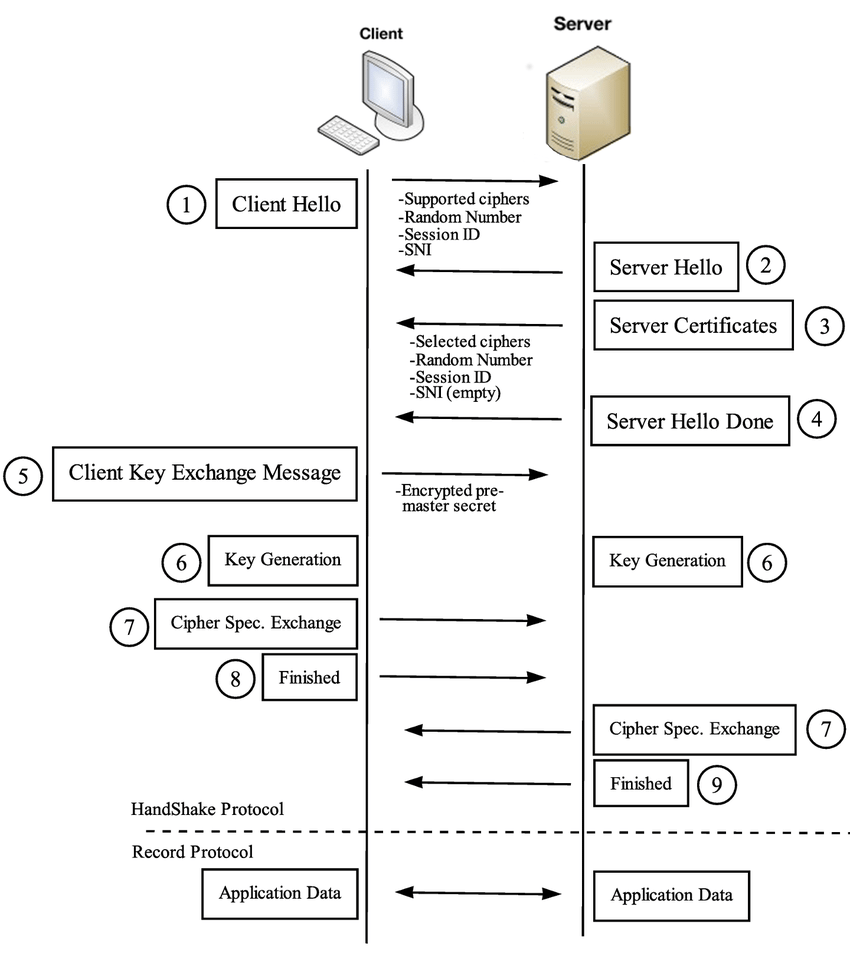
TLS Handshake Steps
- 1) Determines version of TLS and list cipher suites.
- 2) Webserver selects the most secure cipher suite it can support and instructs browser to use those algorithms for comm.
- 3/4) Same time as step 2, the server passes a digital certificate, containing the server name, the certificate authority(who validates Authenticity)
- 5) Browser verifies authenticity with certificate authorities
- 6) The two machines generate a session key that will be used to encrypt the TLS conversation
- 7) Session specifications are set and encrypted communication can take place
Aproximate time it takes to complete TLS Handshake?
- A. About 300 - 400ms
- B. 2 - 3 seconds
- C. About 1 second
- D. 50 - 150ms
- E. 500 - 800ms
Digital Certificates
Suggested Reading
- Forthcoming